The banner came out. We are treated by means of Windows. Dr.Web Computer Unlock Service
Description of the problem: when you open any site in the browser pops up ads. Pop-up viral banners obscure content and web pages load slowly. Clicking on links in the browser opens windows and tabs with ads. This article describes how to remove ads in the browser Google Chrome, Yandex, Opera, Mozilla, Internet Explorer.
An example of a window with third-party banners:
Where do third-party ads come from in the browser?
Why doesn't the antivirus remove ads from the browser?
The banner ad is not a virus per se. The user himself launches a program that makes changes to the system, thinking that he has downloaded a game or something safe. And the antivirus sees that the file was not launched by itself, as is the case with a virus, but it was launched by the user on his own behalf.
How to remove ads in the browser - detailed effective instructions
1 Go to Control Panel and select the item Programs and Features. Carefully review the list of installed programs. Remove the following unwanted programs if they are listed:

Also, Avast's browser cleaner utility can help you:
3 Check your start page settings. Remove the start pages that the virus prescribed. (Instruction for Google Chrome: ) 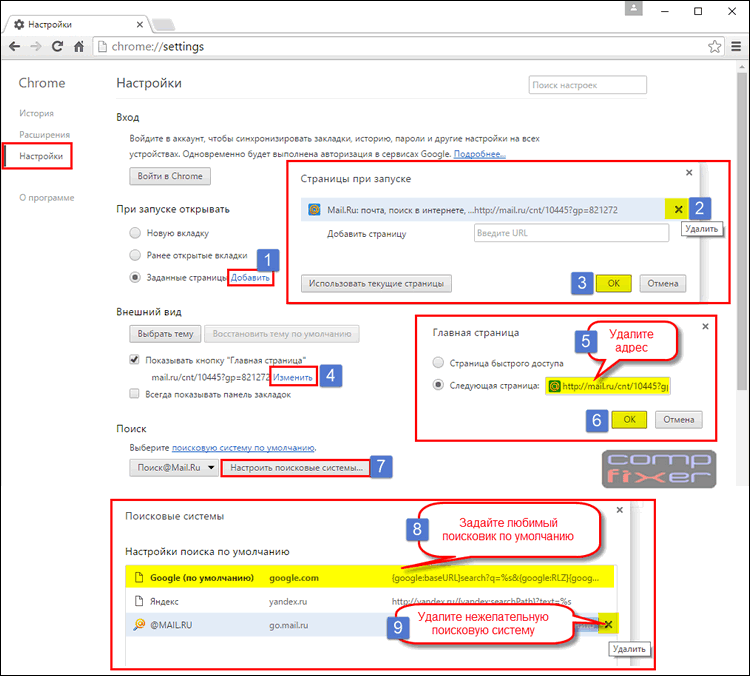
Attention! Instead of points 2 and 3, you can. But note that in this case you will remove everything applications, extensions, settings for search engines and start pages. After the reset, you will have to configure browsers from scratch.

6 Check for changes in browser shortcuts. Most often, malware prescribes the start page there. If in the field An object added the start page of the view http://site-name.ru , then in order to remove ads in the browser, delete the site address and save the shortcut with the OK button:
If you are unable to save the shortcut, check that on the tab General there was no jackdaw Only reading. If it is, remove it and click Apply. After that go to the tab Label, delete the postscript and save the change in the label with the button OK.

Often there are postscripts to go to the following (often malicious) sites:
(do not try to paste these lines into the browser!)
mygooglee.ru
www.pribildoma.com
www.rugooglee.ru
sweet-page.com
dengi-v-internete.net
delta-homes.com
v-inet.net
answerstims.net
business-ideia.net
newsray.ru
default-search.net
7 Install CCleaner. Clean up:
- caches in all browsers;
- cookies;
- cleaning temporary system files;


8 Install MalwareBytes AntiMalware. (Read our article on how to remove ads, malware and viruses with it: )
Update bases.
Perform a full system scan and remove any viruses found that are often the cause of third-party ads in Chrome, Firefox, Opera and other browsers on a computer with any version of Windows:

Removing malware that causes ads in the browser
9 Important point! Download AdwCleaner. ()
Perform a system scan and remove any malware found, then reboot. In many cases, this program alone allows you to completely eradicate ads that appear in the browser due to unwanted extensions:
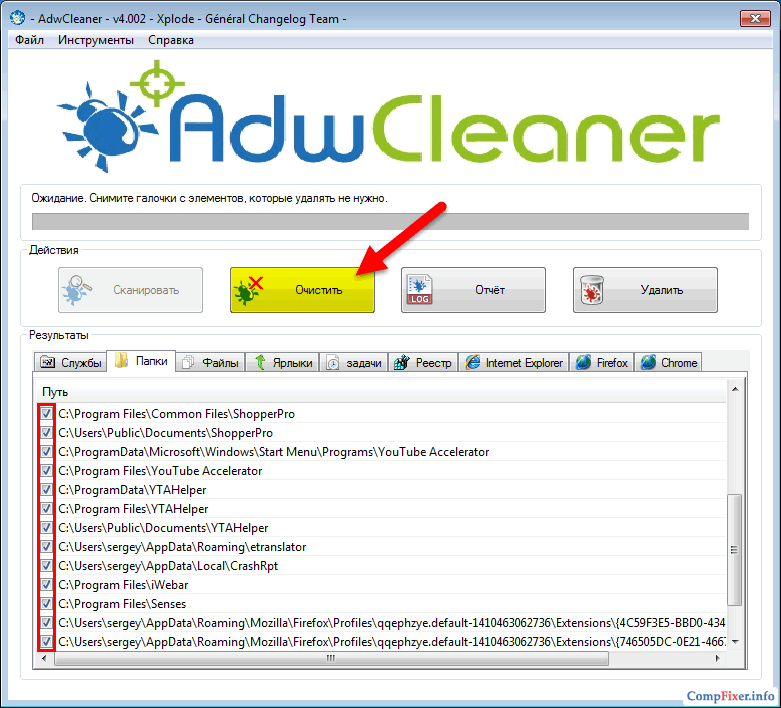
This little program very often helps to remove ads in the browser in just a couple of clicks!
10 Run a system check with a trial version of the program HitmanPro. (Read detailed instructions on registering and using the program:). This powerful utility often helps to get rid of ads, annoying banners and pop-ups that other antiviruses can't handle.

If the steps above do not help, it is most likely that malware has modified browser settings in the registry or has seriously damaged the system. Move on to the next item.
What to do if nothing helped to remove ads in the browser
11 You must remove all browsers and clean the registry manually. How to do it?
- Delete the Opera browser.
- Reboot.
- Delete a folder C:\Program Files (x86)\Opera .
- Run regedit, look in the registry for all keys containing the word opera and delete them manually.
At the same time, you should be careful not to accidentally delete keys that contain similar words, for example, opera tion, opera ting. - Delete the Chrome browser, Firefox and all the rest.
- Reboot.
- Delete their folders from Program Files and Program Files (x86).
- Look for the names of browsers in the keys and names of the registry keys and delete them.
After uninstalling all browsers:
- Do ;
- Install your favorite browser again and look at the result.
- If there are no banners, install other browsers if you need them.
I ask for your participation in my problem. My question is this: How to remove the banner: “Send SMS”, Windows 7 operating system. By the way, the second system on my Windows XP computer was also blocked by a banner a month ago, so I’m such a would-be user. I can’t enter safe mode, but I managed to enter Computer Troubleshooting and from there run System Restore and I got an error - There are no restore points on the system drive of this computer.
The unlock code on the Dr.Web website, as well as ESET, could not be found. Recently, such a banner was removed from a friend using the LiveCD ESET NOD32 System Recovery Disk, but in my case it does not help. Dr.Web LiveCD also tried. I changed the clock in the BIOS forward for a year, the banner did not disappear. On various forums on the Internet, it is advised to correct the UserInit and Shell parameters in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon registry branch. But how can I get there? With LiveCD? Almost all LiveCD disks do not connect to the operating system and such operations as editing the registry, viewing startup objects, as well as event logs from such a disk are not available or I'm wrong.
In general, there is information on how to remove a banner on the Internet, but basically it is not complete and it seems to me that many people copy this information somewhere and publish it on their website so that it would just be, but ask them how it all works , shrug their shoulders. I think this is not your case, but in general I really want to find and remove the virus on my own, I'm tired of reinstalling the system. And the last question - is there a fundamental difference in the ways to remove the ransomware banner in Windows XP and Windows 7 operating systems. Can you help? Sergey.
How to remove the banner
There are quite a few ways to help you get rid of the virus, it is also called Trojan.Winlock, but if you are a novice user, all these methods will require you to be patient, persevere and understand that the enemy is serious for you, if you are not afraid, let's start.
- The article turned out to be long, but everything said really works both in the Windows 7 operating system and in Windows XP, if there is a difference somewhere, I will definitely mark this point. The most important thing to know remove the banner and return the operating system - quickly, it will not always work out, but it’s useless to put money on the extortionists’ account, you won’t receive any response unlock code, so there is an incentive to fight for your system.
- Friends, in this article we will work with the Windows 7 Recovery Environment, or more precisely with the command line of the Recovery Environment. I will give you the necessary commands, but if it is difficult for you to remember them, you can. This will greatly facilitate your work.
Let's start with the simplest and finish with the most complex. How to remove the banner using safe mode. If your Internet surfing ended unsuccessfully and you inadvertently installed malicious code for yourself, then you need to start with the simplest thing - try to enter Safe Mode (unfortunately, in most cases you will not succeed, but it's worth a try), but You will definitely be able to enter(more likely), you need to do the same thing in both modes, let's look at both options.
In the initial phase of loading the computer, press F-8, then choose, if you manage to enter it, then you can say you are very lucky and the task is simplified for you. The first thing to try is to rollback using restore points to some time ago. Who does not know how to use system restore, read in detail here -. If System Restore doesn't work, try something else.

Type msconfig in the Run box,


You should also not have anything in the folder, . Or is it located at
C:\Users\Username\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.
Important note: Friends, in this article you will have to deal mainly with folders that have the Hidden attribute (for example, AppData, etc.), therefore, as soon as you get into Safe mode or Safe mode with command line support, immediately turn on the system show hidden files and folders, otherwise you will simply not see the necessary folders in which the virus is hiding. It is very easy to do this.
Windows XP
Open any folder and click on the " Tools" menu, select " Folder Options", then go to the tab " View" Next, at the very bottom, check the item "" and click OK
Windows 7
Start -> Control Panel->View: Category -Small Icons ->Folder Options ->View. At the very bottom, check the box " Show hidden files and folders».
So back to the article. We look at the folder, you should not have anything in it.

Make sure that there are no unfamiliar and suspicious folders and files in the root of the drive (C :), for example, with such an incomprehensible name OYSQFGVXZ.exe, if there are, they need to be deleted.


Now attention: In Windows XP, we delete suspicious files (an example is visible above on the screenshot) with strange names and
with .exe extension from folders
C:\
C:\Documents and Settings\Username\Application Data
C:\Documents and Settings\Username\Local Settings
C:\Documents and Settings\Username\Local Settings\Temp- delete everything from here, this is a folder of temporary files.
Windows 7 has a good level of security and in most cases will not allow malware to make changes to the registry, and the vast majority of viruses also tend to get into the temporary files directory:
C:\USERS\username\AppData\Local\Temp, from here you can run the executable file.exe. For example, I cite an infected computer, on the screenshot we see the virus file 24kkk290347.exe and another group of files created by the system almost at the same time along with the virus, everything needs to be deleted.

There should not be anything suspicious in them, if there is, we delete it.

And be sure to:
In most cases, the above steps will remove the banner and boot the system normally. After normal boot check your entire computer with a free anti-virus scanner with the latest updates - Dr.Web CureIt, download it from the Dr.Web website.
- Note: You can immediately infect a normally booted system with a virus again by going online, as the browser will open all the pages of sites that you have recently visited, among them there will naturally be a virus site, as well as a virus file may be present in the temporary folders of the browser. We find and, which you used recently at: C:\Users\Username\AppData\Roaming\Browser Name, (Opera or Mozilla for example) and in one more place C:\Users\Username\AppData\Local\Your browser name, where (C:) is the partition with the installed operating system. Of course, after this action, all your bookmarks will be lost, but the risk of getting infected again is significantly reduced.
Safe mode with command line support.
If after all this your banner is still alive, do not give up and read on. Or at least go to the middle of the article and read the full information about fixing registry settings in case of a ransomware banner infection.
What should I do if I can't get into safe mode? Try Safe mode with command line support, there we do the same, but there is a difference in Windows XP and Windows 7 commands.

Apply System Restore.
In Windows 7, enter rstrui.exe and press Enter - we get into the System Restore window.

Or try typing the command: explorer - a kind of desktop will boot up, where you can open my computer and do the same as in safe mode - check the computer for viruses, see the Startup folder and the root of the disk (C:), as well as the directory temporary files: edit the registry as needed, and so on.

To get into Windows XP System Restore, on the command line, type- %systemroot%\system32\restore\rstrui.exe,

to get into Windows XP in the explorer and the My Computer window, as in the seven, we type the explorer command.

here you first need to type the command explorer and you will be taken directly to the desktop. Many people cannot switch the default Russian keyboard layout to English on the command line using the alt-shift combination, then try shift-alt the other way around.

Already here go to the Start menu, then Run.

then select Startup - delete everything from it, then do everything that you did in and the root of the disk (C:), delete the virus from the temporary files directory: C:\USERS\username\AppData\Local\Temp, edit the registry as needed ( all the details are described above.).
System Restore. Things will be a little different for us if you cannot get into Safe Mode and Safe Mode with command line support. Does this mean that you and I cannot use system restore? No, it does not mean that it is possible to roll back using restore points, even if your operating system does not boot in any mode. In Windows 7, you need to use the recovery environment, in the initial phase of booting the computer, press F-8 and select from the menu Troubleshooting your computer,


In the Recovery Options window, select System Restore again,


Now attention, if when you press F-8 the menu Troubleshooting is not available, then you have corrupted files containing the Windows 7 Recovery Environment.

- Is it possible to do without a Live CD? In principle, yes, read the article to the end.
Now let's think about how we will act if System Restore cannot be started by any means or it has been completely disabled. First, let's see how to remove the banner using the unlock code, which is kindly provided by Dr.Web anti-virus software companies, as well as ESET NOD32 and Kaspersky Lab, in this case, you will need the help of friends. It is necessary that one of them go to the unlock service, for example Dr.Web
https://www.drweb.com/xperf/unlocker/
http://www.esetnod32.ru/.support/winlock/
as well as Kaspersky Lab
http://sms.kaspersky.ru/ and entered in this field the phone number to which you need to transfer money to unlock the computer and clicked the button - Search for codes. If the unlock code is found, enter it into the banner window and click Activation or whatever you have written there, the banner should disappear.

Another easy way to remove the banner is using the recovery disk or, as they are also called, rescue from and. The whole process from downloading, burning the image to a blank CD and checking your computer for viruses is described in detail in our articles, you can follow the links, we will not dwell on this. By the way, rescue disks from anti-virus companies are not bad at all, they can be used like LiveCD - perform various file operations, for example, copy personal data from an infected system or run Dr.Web CureIt, a curing utility from a USB flash drive. And in the ESET NOD32 rescue disk there is a wonderful thing that has helped me more than once - Userinit_fix , which fixes important registry settings on a computer infected with a banner - Userinit, branches HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.

How to fix all this manually, read on.
Well, my friends, if someone else reads the article further, then I am very glad to see you, the most interesting thing will begin now, if you manage to assimilate and even more so apply this information in practice, many ordinary people whom you free from the extortionist banner will quite consider you for a real hacker.
Let's not delude ourselves, personally, everything that is described above helped me in exactly half of the cases of blocking a computer with a virus-blocker - Trojan.Winlock. The other half requires a more careful consideration of the issue, which we will deal with.
In fact, blocking your operating system, anyway Windows 7 or Windows XP, the virus makes its own changes to the registry, as well as to the Temp folders containing temporary files and the C:\Windows->system32 folder. We must correct these changes. Don't forget about the Start->All Programs->Startup folder as well. Now about all this in detail.
- Take your time friends, first I will describe exactly where exactly what needs to be fixed is located, and then I will show how and with what tools.
In Windows 7 and Windows XP, the ransomware banner affects the same UserInit and Shell settings in the registry in the
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.
Ideally they should be like this:
Userinit - C:\Windows\system32\userinit.exe,
Shell-explorer.exe




Check everything spell by letter, sometimes instead of userinit comes across, for example, usernit or userlnlt.
You also need to check the AppInit_DLLs parameter in the registry branch HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs, if you find something there, for example C:\WINDOWS\SISTEM32\uvf.dll, all this must be deleted.

HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce there shouldn't be anything suspicious about them.

And be sure to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce

HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell (should be empty) and in general there should be nothing superfluous here either. ParseAutoexec should be equal to 1 .

You also need to delete EVERYTHING from temporary folders (there is also an article on this topic), but in Windows 7 and in Windows XP they are located a little differently:

Windows 7:
C:\Users\Username\AppData\Local\Temp. Viruses especially like to settle here.
C:\Windows\Temp
C:\Windows\
Windows XP:
C:\Documents and Settings\User Profile\Local Settings\Temp
C:\Documents and Settings\User Profile\Local Settings\Temporary Internet Files.
C:\Windows\Temp
C:\Windows\Prefetch
It will not be superfluous to look at the C:\Windows->system32 folder in both systems, all files ending in .exe and dll with the date on the day your computer was infected with a banner. These files need to be deleted.

And now see how a beginner and then an experienced user will carry out all this. Let's start with Windows 7 and then move on to XP.
How to remove the banner in Windows 7 if System Restore was disabled?
Imagine the worst case scenario. Windows 7 login blocked by ransomware banner. System Restore is disabled. The easiest way is to go into the Windows 7 system using a simple recovery disk (you can do it directly in the Windows 7 operating system - described in detail in our article), you can also use a simple Windows 7 installation disk or any of the simplest LiveCD. Boot into the recovery environment, select System Restore, then select the command line

and we type in it -notepad, we get into Notepad, then File and Open.

We go into the real explorer, click My computer.

We go to the folder C:\Windows\System32\Config , here we specify the File type - All files and we see our registry files, we also see the RegBack folder,

in it every 10 days the Task Scheduler makes a backup copy of the registry keys - even if you have System Restore disabled. What can be done here is to delete the SOFTWARE file from the C:\Windows\System32\Config folder, which is responsible for the HKEY_LOCAL_MACHINE\SOFTWARE registry hive, most often the virus makes its changes here.


And in its place, copy and paste the file with the same name SOFTWARE from the backup copy of the RegBack folder.



In most cases, this will be enough, but if you wish, you can replace all five registry hives from the RegBack folder in the Config folder: SAM , SECURITY , SOFTWARE , DEFAULT , SYSTEM .

Next, we do everything as written above - delete files from the Temp temporary folders, look at the C:\Windows->system32 folder for files with the extension .exe and dll with the date on the day of infection, and of course look at the contents of the Startup folder.
On Windows 7 it is located:
C:\Users\ALEX\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.
Windows XP:
C:\Documents and Settings\ All Users\Main Menu\Programs\Startup.
- How do experienced users do the same, do you think they use a simple LiveCD or a Windows 7 recovery disc? Far from friends, they use a very professional tool - Microsoft Diagnostic and Recovery Toolset (DaRT) Version: 6.5 for Windows 7- this is a professional assembly of utilities located on the disk and necessary for system administrators to quickly restore important operating system settings. If you are interested in this tool, read our article.
By the way, it can perfectly connect to your Windows 7 operating system. By booting your computer from the Microsoft Recovery Disk (DaRT), you can edit the registry, reassign passwords, delete and copy files, use System Restore, and much more. Of course, not every LiveCD has such features.
We boot our computer from this, as it is also called, the Microsoft resuscitation disk (DaRT), Initialize the network connection in the background, if we do not need the Internet, we refuse.

Assign drive letters in the same way as on the target system - say Yes, it's more convenient to work this way.



I will not describe all the tools, since this is a topic for a large article and I am preparing it.
Let's take the first Registry Editor tool, a tool that allows you to work with the registry of the connected Windows 7 operating system.

We go to the Winlogon parameter of the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon branch and simply edit the files manually - Userinit and Shell . How important they should be, you already know.

Userinit - C:\Windows\system32\userinit.exe,
Shell-explorer.exe

In our case, you need to clean the Temp temporary folders from everything, how many of them and where they are in Windows 7, you already know from the middle of the article.
But attention! Since Microsoft Diagnostic and Recovery Toolset is fully connected to your operating system, you won’t be able to delete, for example, registry files -SAM, SECURITY, SOFTWARE, DEFAULT, SYSTEM, because they are in progress, but please make changes.
How to remove the banner in Windows XP
Again, the point is in the tool, I suggest using ERD Commander 5.0 (link to the article above), as I said at the beginning of the article, it is specially designed to solve such problems in Windows XP. ERD Commander 5.0 will allow you to directly connect to the operating system and do everything that we did with the Microsoft Diagnostic and Recovery Toolset in Windows 7.
We boot our computer from the recovery disk. Select the first option to connect to an infected operating system.

Select registry.

We look at the UserInit and Shell parameters in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon branch. As I said above, they should have such a value.
Userinit - C:\Windows\system32\userinit.exe,
Shell-explorer.exe

We also look at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs - it must be empty.

Next, go to the explorer and delete everything from the Temp temporary folders.
How else can you remove a banner in Windows XP using ERD Commander (by the way, this method is applicable to any Live CD). You can try to do this even without connecting to the operating system. Download ERD Commander and work without connecting to Windows XP,

in this mode, we will be able to delete and replace registry files, since they will not be involved in the work. Select Explorer.

The registry files in the Windows XP operating system are located in the C:\Windows\System32\Config folder. And the backup copies of the registry files created during the installation of Windows XP are in the repair folder located at C:\Windows\repair .


We do the same, copy the SOFTWARE file first,

and then you can also the rest of the registry files - SAM , SECURITY , DEFAULT , SYSTEM in turn from the repair folder and replace them with the same ones in the C:\Windows\System32\Config folder. Replace file? We agree - Yes.

I want to say that in most cases it is enough to replace one SOFTWARE file. By replacing the registry files from the repair folder, there is a good chance to boot the system, but most of the changes you made after installing Windows XP will be lost. Consider if this method is right for you. Do not forget to remove everything unfamiliar from startup. In principle, the MSN Messenger client should not be deleted if you need it.


And the last way for today to get rid of the ransomware banner using the ERD Commander disk or any Live CD
If you had System Restore enabled in Windows XP, but you can't apply it, then you can try to do this. We go to the C:\Windows\System32\Config folder containing the registry files.

Open the full file name with the slider and delete SAM, SECURITY, SOFTWARE, DEFAULT, SYSTEM. By the way, before deleting them, you can copy them somewhere just in case, you never know what. Maybe you want to play back.

Next, go to the folder System Volume Information\_restore(E9F1FFFA-7940-4ABA-BEC6- 8E56211F48E2)\RP\ snapshot , here we copy files that are backup copies of our registry branch HKEY_LOCAL_MACHINE\
REGISTER_MACHINE\SAM
REGISTRY_MACHINE\SECURITY
REGISTRY_MACHINE\SOFTWARE
REGISTER_MACHINE\DEFAULT
REGISTER_MACHINE\SYSTEM

Paste them into the folder C:\Windows\System32\Config

Then we go to the Config folder and rename them, deleting REGISTRY_MACHINE \, thereby leaving new registry files SAM , SECURITY , SOFTWARE , DEFAULT , SYSTEM .



Then we delete the contents of the Temp and Prefetch folders, delete everything from the Startup folder as shown above. I will be glad if someone helped. In addition to the article, a small and interesting one is written, you can read it.
from the Windows desktop. You probably already know what the banner on the desktop looks like, since you are interested in this article. This problem exists and has existed for a long time. In such an unpretentious way, some not quite conscious individuals earn their daily bread and spoil the nerves of the happy owners of personal computers.
What is a desktop banner?
The banner is A malicious program that blocks Windows and displays an adware module with various requirements:
- send sms to short number
- transfer funds to wallet
- replenish the specified phone account
- make a payment through the terminal



Meet banners a variety of colors and content, but all of them partially or completely block the control of the Windows operating system, depriving the owner of the computer of certain functions, and require money for unlocking and returning to its original state.
Winlocker (Trojan.Winlock)- a computer virus that blocks access to Windows. After infection, it prompts the user to send an SMS to receive a code that restores the computer's performance. It has many software modifications: from the simplest - "introduced" in the form of an add-on, to the most complex - modifying the boot sector of the hard drive.
A warning! If your computer is locked by a winlocker, under no circumstances should you send an SMS or transfer money to receive an OS unlock code. There is no guarantee that it will be sent to you. And if this happens, know that you will give the attackers your hard-earned money for nothing. Don't fall for tricks! The only correct solution in this situation is to remove the ransomware virus from the computer.
Self-removal of ransomware banner
This method is applicable to winlockers that do not block booting the OS in safe mode, the registry editor and the command line. Its principle of operation is based on the use of system utilities only (without the use of anti-virus programs).
1. When you see a malicious banner on your monitor, first turn off your Internet connection.
2. Reboot the OS in safe mode:
- at the time of the system reboot, hold down the "F8" key until the "Additional boot options" menu appears on the monitor;
- use the cursor arrows to select "Safe Mode with Command Line Support" and press "Enter".

Attention! If the PC refuses to boot into safe mode or the command line / system utilities do not start, try removing the winlocker in another way (see below).
3. At the command line, type the command - msconfig, and then press "ENTER".

4. The System Configuration panel will appear on the screen. Open the "Startup" tab in it and carefully review the list of elements for the presence of a winlocker. As a rule, its name contains meaningless alphanumeric combinations ("mc.exe", "3dec23ghfdsk34.exe", etc.) Disable all suspicious files and remember/write down their names.
5. Close the panel and go to the command line.
6. Type the command "regedit" (without quotes) + "ENTER". Upon activation, the Windows Registry Editor will open.
7. In the "Edit" section of the editor menu, click "Find ...". Write the name and extension of the winlocker found in autoload. Start the search with the "Find next ..." button. All entries with the name of the virus must be deleted. Continue scanning with the "F3" key until all partitions have been scanned.
8. Immediately, in the editor, moving along the left column, view the directory:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\Current Version\Winlogon.
The "shell" entry should be "explorer.exe"; the "Userinit" entry is "C:\Windows\system32\userinit.exe,".
Otherwise, if malicious modifications are detected, use the "Fix" function (right mouse button - context menu) to set the correct values.
9. Close the editor and go back to the command line.
10. Now you need to remove the banner from the desktop. To do this, enter the command "explorer" in the line (without quotes). When the Windows shell appears, remove all files and shortcuts with unusual names (that you did not install on the system). Most likely, one of them is the banner.
11. Restart Windows in normal mode and make sure you managed to remove the malware:
- if the banner has disappeared - connect to the Internet, update the databases of the installed antivirus or use an alternative antivirus product and scan all sections of the hard drive;
- if the banner continues to block the OS, use another removal method. It is possible that your PC was hit by a winlocker, which is “fixed” in the system in a slightly different way.
Removal using antivirus utilities
To download utilities that remove winlockers and burn them to a disk, you will need another, uninfected, computer or laptop. Ask a neighbor, friend or friend to use his PC for an hour or two. Stock up on 3-4 blank discs (CD-R or DVD-R).
Advice! If you are reading this article for informational purposes and your computer, thank God, is alive and well, still download the curing utilities discussed in this article and save them on disks or a USB flash drive. The prepared "first aid kit" doubles your chances of defeating the viral banner! Quickly and without unnecessary worries.
1. Go to the official website of the utility developers - antiwinlocker.ru.
2. On the main page, click the AntiWinLockerLiveCd button.
3. A list of links for downloading program distributions will open in a new browser tab. In the "Disk images for treating infected systems" column, follow the link "Download AntiWinLockerLiveCd image" with the number of the older (newer) version (for example, 4.1.3).
4. Download the ISO image to your computer.
5. Burn it to a DVD-R/CD-R using ImgBurn or Nero using the "Burn disc image" function. The ISO image must be written in unpacked form in order to get a bootable disk.
6. Insert the disc with AntiWinLocker into the PC where the banner is rampant. Restart the OS and go into the BIOS (find out the hotkey for entering in relation to your computer; the options are "Del", "F7"). Install the boot not from the hard drive (system partition C), but from the DVD drive.
7. Restart your PC again. If you did everything correctly - correctly burned the image to disk, changed the boot setting in BIOS - the AntiWinLockerLiveCd utility menu will appear on the monitor.

8. To automatically remove the ransomware virus from your computer, click the "START" button. And that's it! No other actions are needed - destruction in one click.
9. At the end of the removal procedure, the utility will provide a report on the work done (which services and files it unblocked and cured).
10. Close the utility. When you reboot the system, go back to the BIOS and specify the boot from the hard drive. Start the OS in normal mode, check its performance.
WindowsUnlocker (Kaspersky Lab)
1. Open the sms.kaspersky.ru page (Kaspersky Lab's official website) in your browser.
2. Click the "Download WindowsUnlocker" button (located under the inscription "How to remove the banner").
3. Wait until the boot disk image of Kaspersky Rescue Disk with the WindowsUnlocker utility is downloaded to the computer.
4. Burn the ISO image in the same way as the AntiWinLockerLiveCd utility - make a bootable disk.
5. Set the BIOS of the locked PC to boot from the DVD drive. Insert the Kaspersky Rescue Disk LiveCD and reboot the system.
6. To launch the utility, press any key, and then use the cursor arrows to select the interface language ("Russian") and press "ENTER".
7. Read the terms of the agreement and press the key "1" (I agree).
8. When the desktop of Kaspersky Rescue Disk appears on the screen, click on the leftmost icon in the taskbar (the letter "K" on a blue background) to open the disk menu.
9. Select "Terminal".

10. In the terminal window (root:bash) next to the "kavrescue ~ #" prompt, type "windowsunlocker" (without quotes) and activate the directive with the "ENTER" key.
11. The utility menu will be displayed. Press "1" (Unlock Windows).
12. After unlocking, close the terminal.
13. Access to the OS is already there, but the virus is still free. To destroy it, do the following:
- connect the internet;
- launch the "Kaspersky Rescue Disk" shortcut on the desktop;
- update antivirus signature databases;
- select the objects to be checked (it is desirable to check all elements of the list);
- with the left mouse button, activate the "Perform object check" function;
- if a ransomware virus is detected from the suggested actions, select "Delete".
14. After treatment, in the main menu of the disc, click "Turn off". At the time of restarting the OS, go to BIOS and set the boot from the HDD (hard drive). Save your settings and boot Windows normally.
Dr.Web Computer Unlock Service
This method is to try to force the winlocker to self-destruct. That is, give him what he requires - an unlock code. Naturally, you don't have to spend money to get it.
1. Copy the wallet or phone number that the attackers left on the banner to buy the unlock code.
2. Log in from another "healthy" computer to the Dr.Web unblocking service - drweb.com/xperf/unlocker/.

3. Enter the rewritten number in the field and click the "Search Codes" button. The service will automatically select the unlock code according to your request.
4. Rewrite/copy all codes displayed in the search results.
Attention! If there are none in the database, use the Dr.Web recommendation to remove the winlocker yourself (follow the link posted under the message “Unfortunately, at your request ...”).
5. On the infected computer, enter the unlock code provided by the Dr.Web service into the "interface" of the banner.
6. In case of self-destruction of the virus, update the antivirus and scan all sections of the hard disk.
A warning! Sometimes the banner does not respond to entering the code. In this case, you need to use another method of removal.
Removing the MBR.Lock banner
MBR.Lock is one of the most dangerous winlockers. Modifies the data and code of the master boot record of a hard disk. Many users, not knowing how to remove this type of ransomware banner, begin to reinstall Windows, in the hope that after this procedure their PC will “recover”. But, alas, this does not happen - the virus continues to block the OS.
To get rid of the MBR.Lock ransomware, follow these steps (Windows 7 option):
1. Insert the Windows installation disk (any version, assembly will do).
2. Enter the BIOS of the computer (find out the hotkey for entering the BIOS in the technical description of your PC). In the First Boot Device setting, set "Cdrom" (boot from a DVD drive).
3. After the system restarts, the Windows 7 installation disk will boot. Select the type of your system (32/64 bits), interface language and click the "Next" button.
4. At the bottom of the screen, under the "Install" option, click "System Restore".

5. In the "System Recovery Options" panel, leave everything as it is and click "Next" again.
6. Select the "Command Line" option from the Tools menu.
7. At the command prompt, enter the command - bootrec / fixmbr, and then press "Enter". The system utility will overwrite the boot record and thus destroy the malicious code.

8. Close the command line, and click "Restart".
9. Scan your PC for viruses with Dr.Web CureIt! or Virus Removal Tool (Kaspersky).
It is worth noting that there are other ways to treat a computer from a winlocker. The more tools you have in your arsenal to combat this infection, the better. In general, as they say, God saves the safe - do not tempt fate: do not go to dubious sites and do not install software from unknown manufacturers.
After restarting the computer, does the monitor display a request to send a paid SMS, or put money into a mobile phone account?
Meet what a typical ransomware virus looks like! This virus takes thousands of different forms and hundreds of variations. However, it is easy to recognize him by a simple sign: he asks you to put money (call) on an unknown number, and in return promises to unlock your computer. What to do?
First, realize that this is a virus, the purpose of which is to suck as much money out of you as possible. That is why do not give in to his provocations.
Remember a simple thing, do not send any SMS. They will withdraw all the money that is on the balance sheet (usually 200-300 rubles are written in the requirement). Sometimes they require you to send two, three or more SMS. Remember, the virus will not go anywhere from the computer, whether you send money to scammers or not. Trojan winloc will remain on your computer until you remove it yourself.
The action plan is as follows: 1. Remove the block from the computer 2. Remove the virus and treat the computer.
Ways to unlock your computer:
1. Enter unlock code and. The most common way to deal with the obscene banner. You can find the code here: Dr.web , Kasperskiy , Nod32 . Don't worry if the code doesn't work, move on to the next step.
2. Try booting into safe mode. To do this, after turning on the computer, press F8. When the boot options window appears, select "safe mode with driver support" and wait for the system to boot.
2a. Now we try restore system(Start-Accessories-Utilities-System Restore) to an earlier checkpoint. 2b. Create a new account. Go to Start - Control Panel - Accounts. Add a new account, restart the computer. When enabled, select the newly created account. Let's go to .
3. Try ctrl+alt+del- the task manager should appear. We launch healing utilities through the task manager. (select the file - a new task and our programs). Another way - hold down Ctrl + Shift + Esc and holding these keys, look for and delete all strange processes until the desktop is unlocked.
4. The most reliable way- this is to install the OS (operating system) on a new one. If you fundamentally need to keep the old OS, then we will consider a more time-consuming way to deal with this banner. But no less effective!
Another way (for advanced users):
5. Booting from disk live CD which has a registry editor. The system has booted, open the registry editor. In it we will see the registry of the current system and the infected one (its branches on the left side are displayed with a signature in brackets).
We find the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon - we are looking for Userinit there - we delete everything after the comma. ATTENTION! The file "C:\Windows\system32\userinit.exe" CANNOT be deleted.);
Look at the key value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell, it should be explorer.exe. Done with the registry.
If the error "Registry editing is prohibited by the system administrator" appears, download the AVZ program. Open "File" - "System Restore" - Check the item "Unlock the registry editor", then click "Perform marked operations." The editor is back.
Run the Kaspersky removal tool and dr.web cureit and scan the entire system with them. It remains to reboot and return the bios settings. However, the virus has NOT yet been removed from the computer.
We treat a computer from Trojan WinLock
For this we need:
- ReCleaner Registry Editor
- popular antivirus Tool removal kaspersky
- well-known antivirus Dr.web cureit
- effective antivirus Removeit pro
- Plstfix registry repair utility
- Program to remove temporary files ATF cleaner
1. It is necessary to get rid of the virus in the system. To do this, launch the registry editor. We go Menu - Tasks - Launch the registry editor. Need to find:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon - we are looking for the Userinit section there - we delete everything after the comma. ATTENTION! The file "C:\Windows\system32\userinit.exe" CANNOT be deleted.);
Look at the key value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell there should be explorer.exe. Done with the registry.
Now select the "Startup" tab. We look through the startup items, check the boxes and delete (lower right corner) everything that you did not install, leaving only desktop and ctfmon.exe. The remaining svchost.exe processes and other .exe processes from the windows directory must be removed.
Select Task - Registry Cleanup - Use all options. The program will scan the entire registry, delete everything permanently.
2. To find the code itself, we need the following utilities: Kaspersky, Dr.Web and RemoveIT. Note: RemoveIT will ask you to update the virus signature databases. An internet connection must be established during the update!
With these programs, we scan the system disk and delete everything that they find. If you wish, you can just in case check all the disks of the computer. It will take much longer, but it is more reliable.
3. The next utility is Plstfix. It restores the registry after our actions on it. As a result, the task manager and safe mode will start working again.
4. Just in case, delete all temporary files. Often copies of the virus are hidden in these folders. This is how even well-known antiviruses can not detect them. It is better to manually remove something that does not significantly affect the operation of the system. Install ATF Cleaner, mark and delete everything.
5. We overload the system. Everything is working! even better than before :).
Winlocker Trojans are a type of malware that, by blocking access to the desktop, extorts money from the user - supposedly if he transfers the required amount to the attacker's account, he will receive an unlock code.
If once you turn on the PC you see instead of the desktop:

Or something else in the same spirit - with threatening inscriptions, and sometimes with obscene pictures, do not rush to accuse your loved ones of all sins.
They, and maybe you yourself, fell victim to extortionists.
How do ransomware blockers get on a computer?
Most often, blockers get on the computer in the following ways:
- through hacked programs, as well as tools for hacking paid software (cracks, keygens, etc.);
- downloaded from links from messages in social networks, sent supposedly by acquaintances, but in fact - by intruders from hacked pages;
- downloaded from phishing web resources that imitate well-known sites, but in fact created specifically for the spread of viruses;
- come by e-mail in the form of attachments accompanying letters of intriguing content: “you were sued ...”, “you were photographed at the crime scene”, “you won a million”, and the like.
Attention! Pornographic banners are not always downloaded from porn sites. Can and with the most ordinary.
Another type of ransomware is distributed in the same way - browser blockers. For example, like this:

or like this:

They demand money for access to web browsing through a browser.
How to remove the banner "Windows is blocked" and the like?
When the desktop is locked, when a virus banner prevents the launch of any programs on the computer, you can do the following:
- go into safe mode with command line support, start the registry editor and delete the banner's autorun keys.
- boot from a Live CD (“live” disk), for example, ERD commander, and remove the banner from the computer both through the registry (autorun keys) and through the explorer (files).
- scan the system from a boot disk with an antivirus, such as Dr.Web LiveDisk or Kaspersky Rescue Disk 10.
Method 1: Removing the winlocker from safe mode with console support.
So, how to remove a banner from a computer via the command line?
On machines with Windows XP and 7, before the system starts, you need to quickly press the F8 key and select the marked item from the menu (in Windows 8 \ 8.1 there is no such menu, so you have to boot from the installation disk and run the command line from there).

Instead of a desktop, a console will open in front of you. To launch the registry editor, enter the command in it regedit and press Enter.

Next, open the registry editor, find virus entries in it and fix it.
Most often, ransomware banners are registered in sections:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon- here they change the values of the Shell, Userinit and Uihost parameters (the last parameter is only in Windows XP). You need to fix them to normal:
- shell=explorer.exe
- Userinit = C:\WINDOWS\system32\userinit.exe, (C: is the letter of the system partition. If Windows is on drive D, the path to Userinit will start with D:)
- Uihost=LogonUI.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows- see AppInit_DLLs parameter. Normally, it may be absent or have an empty value.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run- here the ransomware creates a new parameter with the value as the path to the blocker file. The parameter name can be a string of letters, such as dkfjghk. It must be removed completely.
The same goes for the following sections:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
To fix registry keys, right-click on the setting, select Edit, enter a new value, and click OK.

After that, restart your computer in normal mode and do an antivirus scan. It will remove all ransomware files from your hard drive.
Method 2. Removing a winlocker using ERD Commander.
ERD commander contains a large set of tools for restoring Windows, including when it is damaged by blocker trojans.
Using the ERDregedit registry editor built into it, you can do the same operations that we described above.
ERD commander will be indispensable if Windows is blocked in all modes. Copies of it are distributed illegally, but they are easy to find on the net.
ERD commander sets for all versions of Windows are called MSDaRT (Microsoft Diagnostic & Recavery Toolset) boot disks, they come in ISO format, which is convenient for burning to DVD or transferring to a USB flash drive.

After booting from such a disk, you need to select your version of the system and, by going to the menu, click the registry editor.

In Windows XP, the procedure is slightly different - here you need to open the Start menu (Start), select Administrative Tools and Registry Editor.

After editing the registry, boot Windows again - most likely, you will not see the "Computer is locked" banner.
Method 3. Removing the blocker using the anti-virus "rescue disk".
This is the easiest, but also the longest unlocking method.
It is enough to burn the image of Dr.Web LiveDisk or Kaspersky Rescue Disk to DVD, boot from it, start scanning and wait for the end. The virus will be killed.

It is equally effective to remove banners from a computer using both Dr.Web and Kaspersky discs.
- What was taught to women who became guards in concentration camps Torture used by the Nazis
- Singer Alex Malinovsky: biography, career, personal life, photo Let's start the story again
- Do I need to shave the testicles and how to do it right at home How to shave the eggs
- Chinese girls with small breasts
- Famous girls with small breasts
- Shoulder girdle: why you can’t sympathize with Russian truckers
- How to clean your computer from junk and speed up its work
- Wedding predictions for guests: funny and funny ideas Comic fortune-telling of a gypsy in prose
- Business on coffee grounds or how to open a mobile coffee shop on wheels?
- Congratulation of a gypsy on a woman's anniversary
- Define the concepts: choir, vocal ensemble, trio, duet, solo
- Guy's Room Design: Ideas and Examples
- General rules for drawing up a foundation plan House foundation drawings
- modern art deco bedroom small art deco bedroom
- Pansies: characteristics and photos of flowers
- Making an art deco bedroom: the choice of materials Beige art deco bedroom
- Bedroom interiors in art deco style Bedroom art deco style beige
- Young: planting and care in the open field Young planting and care in the open
- Varieties for open ground
- Pansies: cultivation and care in the open field









